Forskning
Before the project starts
Research planning, approval, and fundraising steps (and expected timeline)
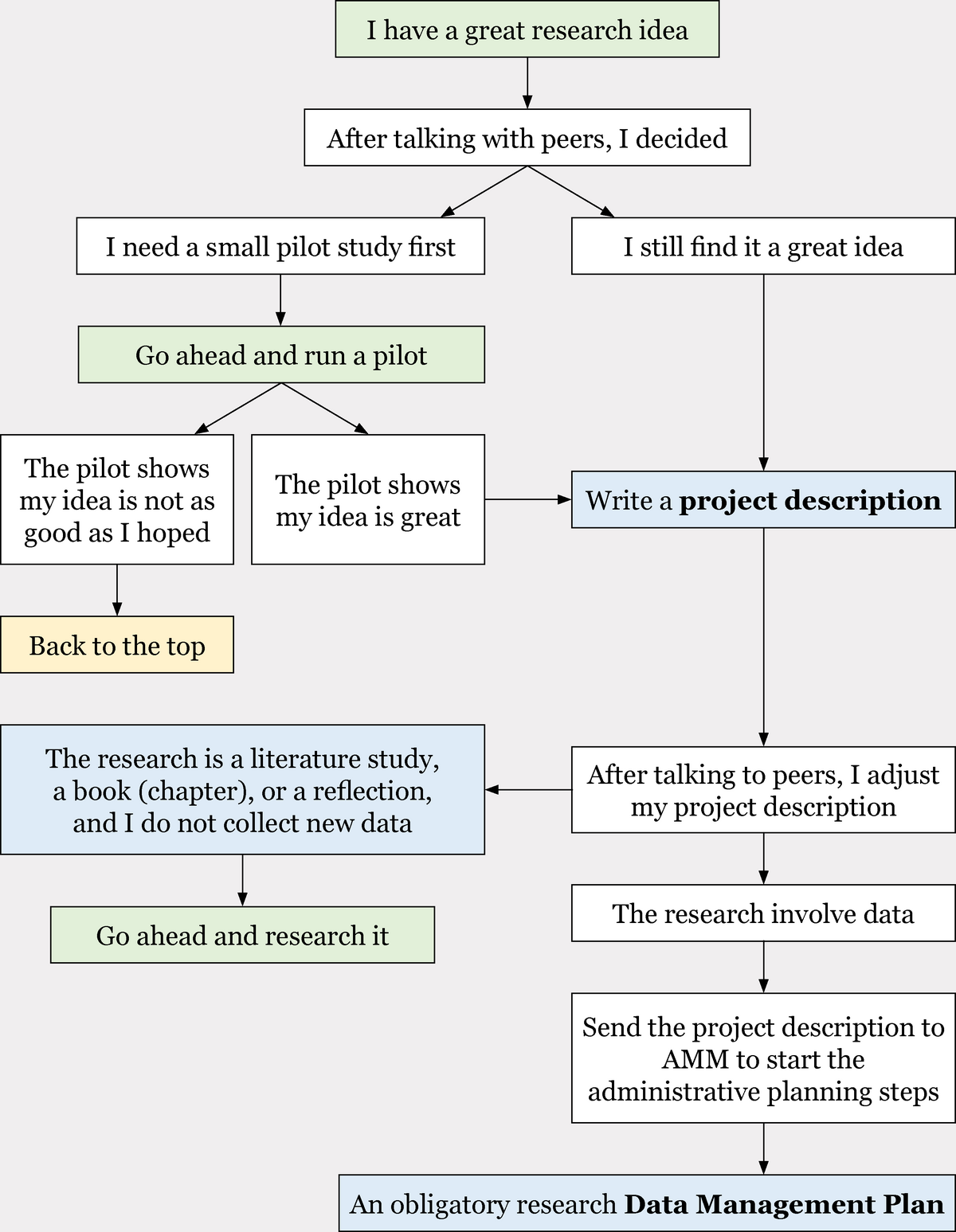
Step 1: Project description
All research projects with a CED employee as principal investigator must use the template below.
Principal investigators are encouraged to present their preliminary project description for the CED research group to get feedback and inspiration that can improve the project.
Fill in the items in the Word document below, maximum 5 pages, and send it to AMM.
What happens then?
Expect up to 2 weeks for her approval response.
AMM reads the project description, and one of three things can happen:
- Approval – proceed to step 2
- Some questions from AMM that can be clarified in a mail-correspondence or a meeting, after which you adjust the project description and go to step 2
- Re-classification as a quality assurance or development project that AMM can exempt from the following steps proceeding directly to get it going
Step 2: Data Management Plan
All research projects involving data and with a CED employee as principal investigator must include a written data management plan. Please, use the dynamic DeiC template link below.
The data management plan should answer the following five questions:
- What type of data is going to be collected during the research project?
- How are the collected data classified and risk assessed?
- Non-sensitive personal data, like name, age, gender, e-mail, location
- Typically, very low risk
- Sensitive personal data, like ethnic origin, political party membership, trade union membership, biometric data (like DNA), health data, sexual orientation
- Can result in a higher risk assessment limiting where data can be stored and how, and how it can be shared
- Non-sensitive personal data, like name, age, gender, e-mail, location
- Where and how are the collected data (safely) kept?
- Who from the research team is responsible for the collected data?
- With whom and how are data shared (outside of CED)?
Principal investigators are encouraged to present their preliminary data management plan for the CED research group to get feedback and inspiration that can improve data quality.
Principal investigators can also contact the CED liaison librarian (Alexandra Fogtmann-Schulz) for help.
Fill in the DeiC template below and send it to AMM.
What happens then?
Expect up to 2 weeks for her approval response.
AMM reads the data management plan, and one of three things can happen:
- Approval – go ahead and research it
- Some questions from AMM that can be clarified in a mail-correspondence or a meeting, after which you adjust the data management plan
- Approval – followed by one or several of the following approval steps as shown in the flow chart in step 3 below
DeiC DMP
The DeiC DMP is a tool for writing data management plans. The DeiC DMP must be filled in and sent to AMM before the start of the project.
It is a good idea to prepare ahead. The DeiC DMP will ask you to fill in the following information:
1. Project details
What research project are you planning?
(If applying for funding, state the project title exactly as in the proposal)
or
Tick box: Mock project for testing, practice, or educational purposes
Select the primary research organization:
Aarhus University
Select the primary funding organization
or
Tick box: No funder associated with this plan or my funder is not listed
2. Project details
Project abstract: Briefly summarise your research project to help others understand the purposes for which the data are being collected or created.
Project start: fill in date Project end: fill in date
ID: A pertinent ID as determined by the funder and/or by the organisation
Funder
Funding status: choose between: planned, funded, denied
Grant number/ URL
→ Save
3. Contributors
Please list the project’s Principal Investigator(s) and those responsible for data management.
Fill in for each contributor: Name, e-mail, ORCID (if relevant), affiliation, role (data manager, principal investigator, project administrator, other – multiple selection is possible)
→ Save and add additional contributors
4. Plan overview
Consider the questions below
- Data Collection
What data will you collect or create?
How will the data be collected or created? - Documentation and Metadata
What documentation and metadata will accompany the data? - Ethics and Legal Compliance
How will you manage any ethical issues?
How will you manage copyright and Intellectual Property Rights (IPR) issues? - Storage and Backup
How will the data be stored and backed up during the research?
How will you manage access and security? - Selection and Preservation
Which data are of long-term value and should be retained, shared, and/or preserved?
What is the long-term preservation plan for the dataset? - Data Sharing
How will you share the data?
Are any restrictions on data sharing required? - Responsibilities and Resources
Who will be responsible for data management?
What resources will you require to deliver your plan?
→ Write plan (on the basis of the questions above)
5. Share
Set plan visibility
- Private: restricted to you and your collaborators.
- Organisational: all registered DMPonline users from your organisation can view.*
- Public: anyone can view your plan in the Public DMPs list.*
*Public or organisational visibility is intended for finished plans. You must answer at least 50% of the questions to enable these options.
Manage and invite collaborators
Fill in emails and permissions (co-owner, editor, read only)
6. Download
Choose format and settings (eg. PDF, font etc.)
Liaison librarian
Videos about research data management
Within the framework of the National Forum for Research Data Management, Danish universities have created videos about research data management. There are three videos: Introduction, FAIR principles, and data management plans.
Each video is about 20 minutes.
Instructions for storage and processing of research data
Research data management may be perceived as a troublesome task, but it offers many advantages. For example, good data management can:
- help your peers and yourself to understand your research project and its data
- make it easier to collaborate and share data
- make your research more visible, which in turn can lead to more citations
- make your research more transparent, reliable and reproducible
- avoid data loss.
Remember that you must always comply with AU's "Instructions for storage and processing of research data".
Get an overview of how to process data in the various phases of your research: https://medarbejdere.au.dk/en/research-data-management.
Step 3: Potential approvals
The CED management is held accountable for our compliance and contract signatures are made by AMM.
The flow chart below shows a standard pathway though the external approvement steps, but please, note that not every project needs to go through all of them.
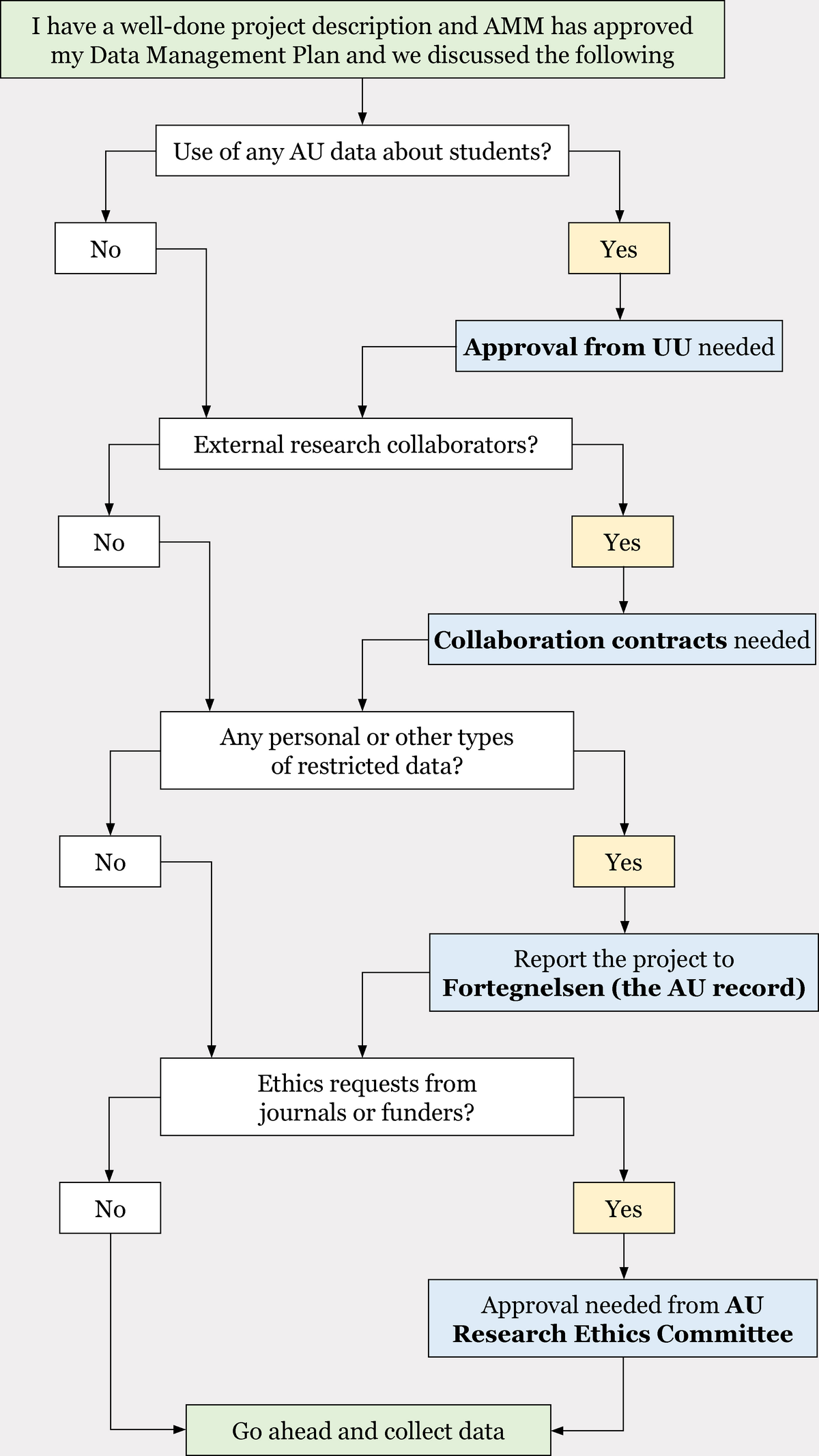
Approval from UU
For approval from the Education Committee (UU – Uddannelsesudvalget), please contact AMM.
The UU must approve all research projects that include use of AU student data.
Expect 4-8 weeks of approval time depending on our timing and their schedule.
Collaboration contracts and data processing agreements
In some cases, it is a requirement to enter a written collaboration contract.
The AU ground rules for obligatory written collaboration agreements are:
- If the central principles for freedom of research, arm’s length, impartiality, honesty, transparency, or responsibility, may be put under pressure during the project?
- If the external funder is also a partner in the research project?
- If the external funding is to be shared between AU and another external partner?
- If there are specific conditions attached to the external funding?
- If the external collaboration involves sharing of personal data?
Read more: Written collaboration agreement – when & why?
If you can answer no to the above five questions, a contract might not be necessary. Talk to AMM.
If you can answer yes to any of the above questions, continue reading.
Does the project fall into A or B:
A) Projects that collaborate with one other Danish or EU university:
The CED use the standard fast track collaboration contract: Fast track Agreements
Note that the the CED-signature is usually AMM (Institutleder / centerleder for AU), so talk to her about it when we discuss the data management plan in step 2.
Furthermore, we also need a signed shared data agreement or a data processing agreement:
- the shared data agreement if you and the partner institution share responsibility
- a data processing agreement if you have data responsibility
Read more: Data controller or data processor (au.dk)
If necessary, TTO can help with these contracts. We can contact senior legal advisor Henriette Within Hansen (hwh@au.dk), who has very kindly offered to assist us directly.
Expect 4-8 weeks for standard contracts to be signed by all.
B) Projects that involve multi-institutional collaboration, collaboration outside EU or collaboration with a private company should always be assisted by TTO up front in this step.
Expect this to take time – several months is not unusual.
Fortegnelsen (the AU record)
Remember to register processing of personal data to the record:
If you are processing personal data in connection with a research project, a database, or biobank, it must be registered on AU's record before you start.
Here you can find information about the AU record and report your project: https://medarbejdere.au.dk/informationssikkerhed/databeskyttelse/saerligt-om-forskning/anmeld-projekt-til-fortegnelsen
Remove registration of processing of personal data from the record
When you have completed your research project, you must first find out whether it is still necessary to store personal data in accordance with the rules regarding responsible conduct of research or according to the rules in the special legislation.
To remove registration of processing of personal data from the record: https://medarbejdere.au.dk/en/informationsecurity/data-protection/for-scientific-staff/remove-project-from-the-record
Data offboarding
As an employee at the CED, you need to decide what will happen to your research data if your employment at the CED ends (i.e. data offboarding).
You have three choices:
- Data must be deleted. Here you need to pay attention to the Danish Code of Conduct for Research Integrity (in Danish: Den danske kodeks for integritet i forskning), which stipulates that data should be kept for at least five years from the date of publication.
- Data must be archived at CED. Here you need to appoint a new contact person for your research data.
- Data must be passed on to a new institution/place of employment. First, it needs to be assessed whether a transfer is possible and then a transfer agreement must be in place.
AU Research Ethics Committee
When you have gone through all of the above steps, you need to get your studies approved by the Research Ethics Committee:
Fundraising
Finding potentially relevant funds
To get a heads-up about possible upcoming deadlines for funds not supported by the Research Support Office, sign up on the Pivot-RP database, which can help you find funds that are relevant to your project.
Pivot-RP is an external fund database with extensive coverage of European and other foreign external grants in all subject areas.
All employees at AU and regional employees have access to the database, and once you have created a user account, the results of the searches can be saved, downloaded, or shared with colleagues.
- Access the database by creating a user account under 'Create account'.
Find introductory and learning videos for Pivot-RP here: Training - Ex Libris Knowledge Center.
Preparing and visualising own bibliometrics
For help regarding citations, H-Index, visualisation of personal research flow, and collaborations, contact:
Feedback on application content
Collegial feedback from other CED researchers and international research colleagues is essential for application success.
Therefore, we expect all PI at the CED to seek peer feedback at the CED or from international colleagues before sending their application.
We expect all senior researchers at the CED to give collegial feedback willingly and constructively when asked, either at research group meetings or between them after direct agreement between teams.
Budgeting
Ask Birthe Tillgaard for help. She has dedicated time for research application budgets. She is also the CED internal controller and follows the project in all its phases if fundraising succeeds.
Language feedback and proofreading
Ask Lone Folmer Nielsen for help. She has dedicated time for text commenting and proofreading and a MA in Rhetoric.
Approval
Most foundations expect explicit management approval. Contact AMM.
Guiding principles for the use of external funds
The CED employees are continuously involved in projects and activities that are financed by external funding. We want to actively increase the CED’s external funding so more employees will, hopefully, get to have (parts of) a task financed by grants of various kinds. Therefore, this section outlines the guiding principles for the use of such funds.
First and foremost, please note that whether you have raised the funds yourself or are the project owner, all funds in the CED’s account system are public and belong to the university, not the individual employee. Administration rules must always be followed and the CED’s management must be able to account for how the funds have been used. Therefore, both the management and the CED’s internal finance officer (Birthe Tillgaard) are keeping an eye on your administration of external public funds. The management also has opinions on how funds are spent. We have a duty to have that.
Externally funded research and development projects
The project owner must operate within the budget framework, which is divided into individual budget items, for example, meetings and conferences, student workers, or technical equipment. Expenses exceeding the budgeted amount for an individual budget item must always be approved, even if there are available funds for other budget items within the budget framework. In case of doubt, discuss the matter with your immediate manager. All plans for any hiring (except for the use of student workers) must be explicitly discussed with the immediate manager before being initiated. Quarterly, AMM reviews larger grants.
Other externally funded activities
Activities in this category include for example, income from ordinary FTE-based teaching, courses organised by the graduate schools, or salary reimbursement from projects anchored outside the CED. These activities are seen as part of the employee’s task portfolio. Therefore, the funds go to the CED. Employees can, of course, discuss their wishes for the use of the funds with their immediate manager.
GDPR and cyber security
Data protection (GDPR): Personal data and research
Personal data is any type of information that can be attributed to a specific person, even if the person can only be identified if the data is combined with other information.
When working with personal data as part of your research, it is important that you comply with relevant legislation. Here you can gain an overview of what you need to know about GDPR. Follow the steps in the link on what to do BEFORE, DURING, and AFTER your project:
E-learning course: Research Integrity at Aarhus University
You can access the e-learning course ‘Research Integrity at Aarhus University’ in Brightspace. The course is only available to academic staff members, for whom it is mandatory.
Dealing with foreign interference and espionage
In collaboration with the Center for Cyber Security and the Ministry of Higher Education and Science, the national security and intelligence service (PET - Politiets Efterretningstjeneste) has created a handbook with advice for researchers and employees on handling foreign interference and espionage.
They offer 10 security tips:
- Beware of the threat
- Assess the value of your research
- Know relevant legislation
- Know your international partners
- Take good care of your employees and colleagues
- Focus on IT security
- Focus on physical security
- Set the framework for visitors
- Be careful when travelling
- Report what you see
You can read more in the handbook here:
- Is your research at risk? (in Danish: Er jeres forskning i fare?)
Support for your Research Practice
Find information, guidance and tools to support your research practice: https://medarbejdere.au.dk/en/administration/research-support-and-collaboration.



